Cybersecurity Posture Assessment
Included in your posture assessment:
guided Assessment
Through a series of questionnaires, we create a full assessment and gap analysis of your current risk level and cyber posture, compared to industry benchmarks. This includes not only Technology, but, much more importantly, People and Processes.
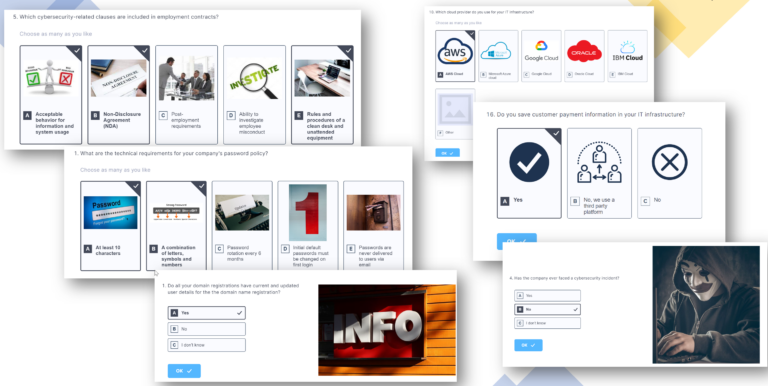
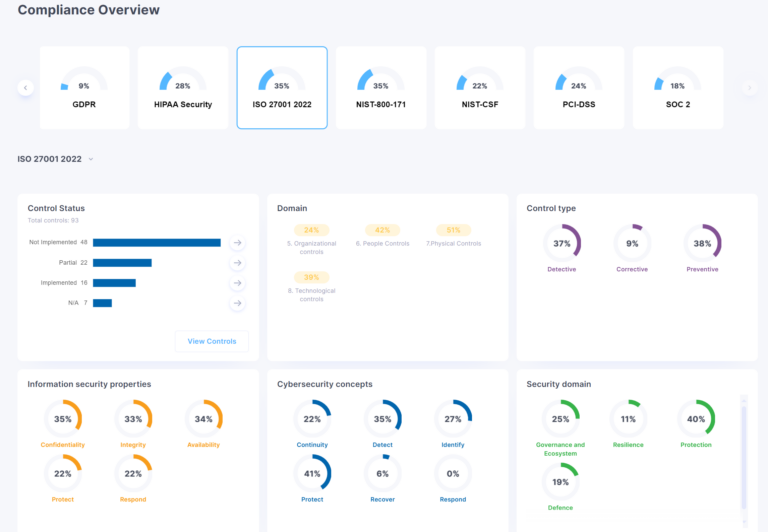
Cybersecurity Posture Analysis report
We provide a detailed Posture Analysis report, including KPIs, your posture chart, and the recommendations for the immediate remediation of underlying risks and critical vulnerabilities.
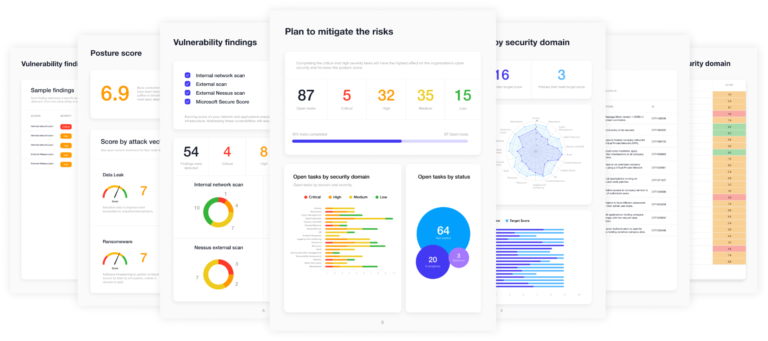
Risk mitigation plan
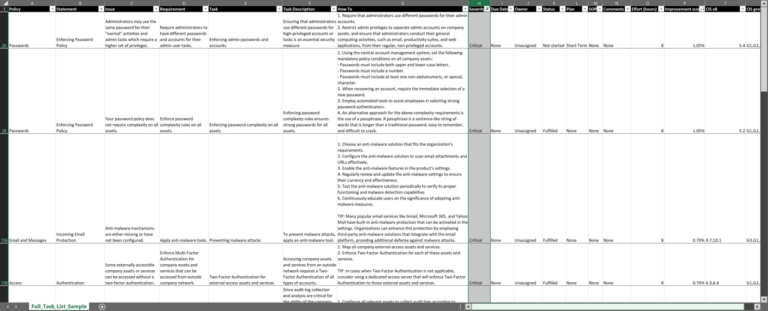
We design a cybersecurity plan bringing the organization to the desired level of protection and compliance. It includes remediation tasks and a detailed implementation plan, sorted by criticality and improvement score.
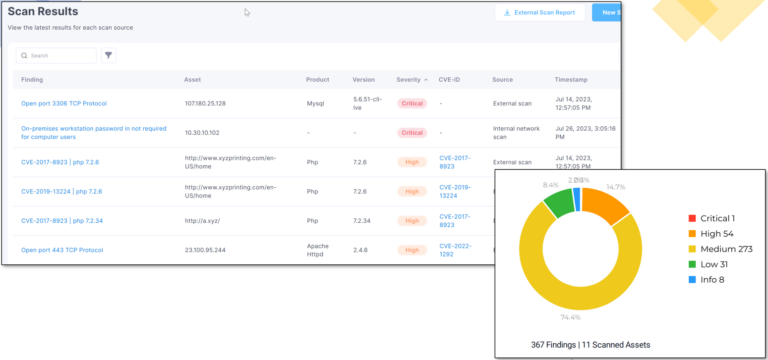
Vulnerability Analysis
A vulnerability scan checks software and systems for security gaps that hackers could exploit and should be done proactively to address risks before they turn into breaches.
Compliance report
Is your client asking for you to be compliant with a specific cybersecurity framework? Are you selling or planning to sell to the government or export to USA or Europe?
If required, we will include a cybersecurity compliance report, a document providing an overview and assessment of your organization’s security policies, controls, and procedures compared to relevant industry standards and cybersecurity frameworks.

how do we work:
Typically, we meet with the business owner and person in charge of IT, to understand your current posture and review your security requirements.
We make it simple. We guide you thru the assessment, and help answer every question. Once completed, review your online assets, analyze and understand all information, and provide you with a comprehensive report indicating where you stand.
